Your Computer is Vulnerable to the Latest Hack Attack – Unless you Have Norton 360
- Comments: 18
- Written on: February 1st, 2011
Most computer users try to be safe when they are online. Many people won’t open emails from people they don’t know. Some only go to websites they know they can trust.
But if you think you are safe online because you are careful, think again.
Microsoft has announced a new security vulnerability was discovered that allows hackers to install malware on any computer from Windows XP up through Windows 7 and all you have to do is visit a website to infect yourself.
This means that you (and 900 million other people) just became a target and all the hackers have to do is get you tto visit an infected website, deliver an infected ad to your computer, or just wait for you to make one fatal typo in your browser’s address bar.
How Can my Computer be Attacked?
With this specific vulnerability an attacker needs to get your browser to load something from an infected website. Some possible ways your computer could be infected include:
- You click on a link in an email taking your to the infected website
- A trusted website displays an advertisement from an infected website
- You mistakenly type an incorrect URL in your address bar
- Your visiting crazy Uncle stupidly just goes to the site an infects your computer
Once your computer is attacked it can sit for hours, days or even weeks before exhibiting signs of infection.
What Do I Need to Do to Stay Safe?
It is always a good idea to employ the safe computing practices I listed at the beginning of this article.
The only security software that Schrock Innovations recommends for its customers is Norton 360 because it is literally the only software program that we have installed for our customers that keeps them safe.
In fact, if you are running Norton 360 you don’t have to worry about the vulnerability discussed in this article at all because Norton has already covered it for you.
If you are not running Norton and want to switch to keep your computer safe, Schrock Innovations has Norton 360 on sale through February 6, 2011.
For only $79.99 Schrock will log into your computer over the Schrock Desk remote support service, clean any infections in your computer, install Norton 360 and configure it for only $79.99!
Contact Schrock Innovations to take advantage of this special offer before it runs out!
Nearly Half of all Scanned Computers are Infected
- Comments: 12
- Written on: February 3rd, 2010
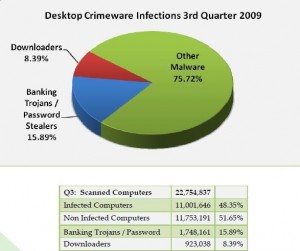 The Anti Phishing Working Group reported that in the third quarter of 2009, 48% of the computers scanned for malware were infected with downloaders, password stealers, or other forms of malware.
The Anti Phishing Working Group reported that in the third quarter of 2009, 48% of the computers scanned for malware were infected with downloaders, password stealers, or other forms of malware.
Their report also indicated a 5.5% increase in reports of first time phishing attempts, with an overall decrease in the number of victims.
This indicates that cyber criminals are working faster to get new phishing sites online, but those sites are being discovered and neutralized more quickly than ever.
The report continues on to indicate that the single greatest problem in the battle against phishing scams is a general lack of awareness among those in the public about how the scams work and how to avoid becoming a victim.
Alpha Anti-Virus Fake Alert Hitting Computer Users
- Comments: 12
- Written on: October 29th, 2009
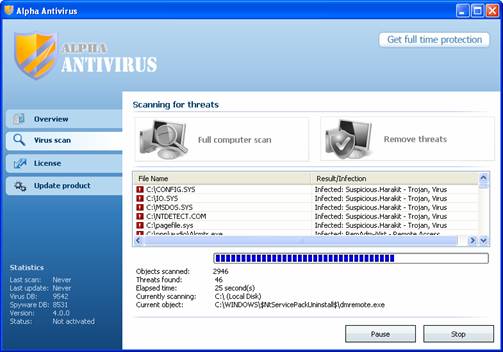 Alpha Antivirus is the latest fake-alert virus that is afflicting computer users on the Internet.
Alpha Antivirus is the latest fake-alert virus that is afflicting computer users on the Internet.
This variant popped up in late September, but is gaining traction as injected websites begin drifting to the top of search engine results.
How Do You Get Infected?
These fake alert infections typically come into your computer through internet web searches on search engines like Google, Yahoo, and Bing.
The makers of these fake-alert infections create thousands of websites with valuable content on subjects they can easily rank in the top 10 results of popular web searches.
After these sites climb to an appropriate level, click-jacking code is inserted that will infect unprotected computers as soon as they visit the page – without warning.
Typically the only symptom of impending infection is a pop-up that warns you that your computer is infected (when it is in fact not).
How Do Keep My Computer Safe?
The best way to keep your computer safe is to have good virus protection software installed on your computer.
While technicians disagree to a degree on which program is the best to use, my opinion (based on HUNDREDS of infected PCs that Schrock Innovations has repaired) is that free antivirus like AVG is a problem waiting to happen.
I recommend Symantec’s Norton 360 software. It offers some of the best protection on the market while also featuring the most user-friendly interface.
Those who are have had bad experiences with Norton in th past because it slowed dow their computers should note that the newer versions are MUCH lighter than the older versions (although any antivirus software will slow down your computer).
Earn Big Money by Infecting Macs With Malware
- Comments: 4
- Written on: October 1st, 2009
 An affiliate network called the Partnetka is working hard in Russia to bring malware to your beloved Mac at a bounty of $.43 per infection.
An affiliate network called the Partnetka is working hard in Russia to bring malware to your beloved Mac at a bounty of $.43 per infection.
Affiliate networks are nothing new on the web – in fact they are much more common than you might imagine. The basic concept is that webmasters run websites that people go to. They use their websites to promote products and services and gt a piece of the action when people buy.
It turns out that according to ZDnet that this network was offering a $.43 payment for every Mac that could be infected and handed over.
Most Mac infections come in the form of DNS changing Trojans that are downloaded in relation to porn videos.
Affiliate networks are pay-for-performance deals. This means that someone out there somewhere intends to make more than $.43 on every Mac they can infect. The days of the Mac being an invincible platform are clearly numbered.
Google Video Poisoned With Malware
- Comments: 1
- Written on: January 28th, 2009
Dancho Danchev posted on ZDNet yesterday about 21 websites that were successfully gaming Google Video and using the service as a delivery vehicle for malware.
The whose scheme is a simple black hat concept. The attackers are using 21 domains to host pages containing YouTube video content. When the Google bot comes to crawl the sites, it sees the videos and ranks them in the Google search results.
This is where the magic happens.
Antivirus 2009 Malware – How to Avoid Infection
- Comments: 6
- Written on: September 25th, 2008
Antivirus 2009, XP Antivirus and XP Antivirus 2008 infections may be using a new exploit to get into PCs that are not equipped with the latest anti-virus software.
New Malware Threat Targets Mozilla FireFox
- Comments: 0
- Written on: September 16th, 2006
A new chapter in the history of Mozilla’s Open Source browser, FireFox, was started this week as the first ever recorded FireFox malware infection was reported. The infection reportedly caused popups to appear on the users computer and defied all reasonable attempts at removal. The Schrock Innovations MCHE research team has investigated this infection, and […]
Stealth Malware on the Horizon
- Comments: 0
- Written on: August 1st, 2006
As more and more big security players create products to help consumers rid their computers of Malware, the creators of the malware are incorporating a new tool into their arsenal – stealth.
It is estimated that 90% of all computers are infected with some degree of Malware (malware is a global term that encompasses spyware, adware, and scumware). Typically systems become infected when users install software programs from the Internet that contain the malware as an additional component.
Database of Spyware a Valuable Resource
- Comments: 0
- Written on: June 8th, 2006
I have teamed up with two other individuals to help launch a new anti-spyware website. It is located at http://www.databaseofspyware.com and it is designed to act as a global repository of all Spyware, Malware, and Adware infections. Eventually we will have manual removal instructions for all of the 7,500 infections that are currently housed on the site.
Spyware Quake Removal Tutorial
- Comments: 4
- Written on: May 7th, 2006
You guessed it… Another wonderful spyware infection is causing problems for our customers. This infection is a variant of the SpyFalcon infection. We detailed its removal
with our Remove SpyFalcon Tutorial.
This new variant will not respond to those removal instructions, so we have created a new tutorial to deal with it. If you think you have the SpywareQuake spyware infection, or are not sure if you do, you can take a look at our Remove Spyware Quake tutorial on our DIY website. The tutorial has pictures of what the screenshots look like and everything.
